The threat of Intentional Electromagnetic Interference (IEMI) has been growing in concern by experts and entities worldwide. Several essential sectors can be targeted by IEMI. They include, for example, power systems, banking systems, water supply, and telecommunications and transportation infrastructures. In addition to onshore assets, IEMI can affect maritime vessels, which perform key economic roles on a global scale.
As part of a collaboration with RH Marine during my secondment, I investigated how the intentional use of electromagnetic interference can affect ships. In this blog, I describe the three ways this can occur due to the threats of jamming, spoofing, and deployment of high-power electromagnetic (HPEM) sources.

Figure 1: Fictitious representation of an attack on a maritime vessel. Photo extracted from [1].
1) Jamming
Today’s maritime vessels depend heavily on Global Navigation Satellite System (GNSS) for safe operations. While GPS (USA) is the most dominant GNSS within the marine and other sectors, other nations have their own systems to provide complementary and independent PNT capacity. The other main GNSSs include Galileo (EU), GLONASS (Russia), and BeiDou (China). Under the scope of ship applications, GNSS is employed for open sea navigation, harbour approaches, vessel positioning monitoring, and situational awareness involving obstructions and other vessels at sea. This high dependency, however, has raised concerns about the vulnerability of these satellite-based systems to electromagnetic interference.
The power of GNSS signals transmitted from satellites to the earth’s surface reaches receivers at very weak levels. According to [2], the transmission power of the main GPS carrier signals, L1 (1575.42MHz) and L2 (1227.6 MHz), is guaranteed at the earth’s surface with minimum power levels below – 166 dBW. Therefore, GNSS receivers of maritime vessels can suffer Denial of Service (DoS) by in-band interference signals that overpower the legitimate signals coming from the satellites. Such RF interference is generally unintentional but can also be purposely generated by individuals with criminal intent.
The probability of detecting GPS signals is proportional to the carrier-to-noise ratio C/N0. The purpose of an intentional jammer is to increase the noise level at the GPS’s operational frequency to prevent the GNSS receiver from detecting the intended signal [3]. Figure 2 illustrates a scenario where a vessel carrying a GPS-based system is targeted by a jammer located on a smaller vessel. In this case, before the attack, the ship navigates according to GPS coordinates. However, it stops acquiring GPS signals once the jammer on the perpetrator’s boat overpowers the legitimate signals coming from the satellites.
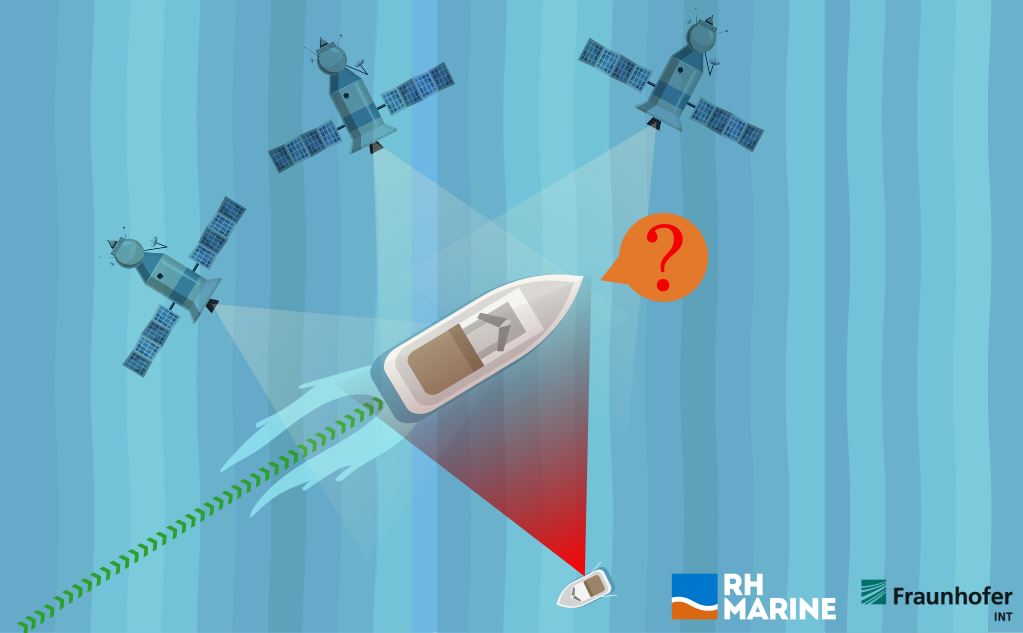
Figure 2: Fictitious representation of an attack on a maritime vessel. Photo extracted from: [1]
In complement to satellite-based systems, naval vessels have additional means of navigation to provide safer navigation. However, given the greater reliance on satellite navigation and accuracy, the incapacity of a vessel’s crew to identify a jamming attack and fall back on traditional means of navigation can make DoS of GNSS signals a safety issue. In the occurrence of GPS signal interruption, alarms linked to the failure of different GPS-dependent functions can sound simultaneously and create a stressful situation in the crew, as shown in the study by [4]. In these conditions, a significant impact on the crew’s safety can arise, especially if the attack occurs when the vessel is performing a highly precise manoeuvre, such as docking in poor light and visibility conditions (e.g., during a storm or foggy night). Therefore, although the vessels have redundant navigation aids, the impact of disrupted satellite navigation aids can have substantial consequences.
2) Spoofing
Transmitting false GNSS-type signals to cause receivers to wrongly compute positions required expensive hardware and could only be performed by RF specialists. Nevertheless, following the introduction of low-cost, software-defined RF signal generators, widespread concern about spoofing attacks on GNSS-dependent systems has been flagged as a security threat. Although there are highly sophisticated military-grade GNSS spoofing sources, low-cost spoofers can nowadays be assembled by perpetrators with minimum RF knowledge.
Assuming that a vessel follows a route set by the GPS in automatic mode, Figure 3 illustrates a scenario where a spoofing attack targets a vessel. In this scenario, a spoofer is located on a small boat, which follows the navigation course of the target vessel. The attack starts when the perpetrator transmits counterfeit signals initially synchronized with the genuine GPS signals acquired by the target GNSS antenna. At a certain point, the power of the spoofed signals is gradually increased until the GNSS receiver acquires them instead of the legitimate signals. Once the receiver is taken over, the perpetrator applies small increments to the target’s positioning, causing the vessel to drift off its planned course. This form of spoofing is termed ‘’carry-off”. Its consequences include collisions, blocked navigation routes, and even piracy attempts. Nevertheless, despite the high risk, “carry-off” attack spoofing attempts require a high technical level of expertise to be accomplished without being detected by the basic anti-spoofing algorithms found in some GNSS receiver technologies [5].
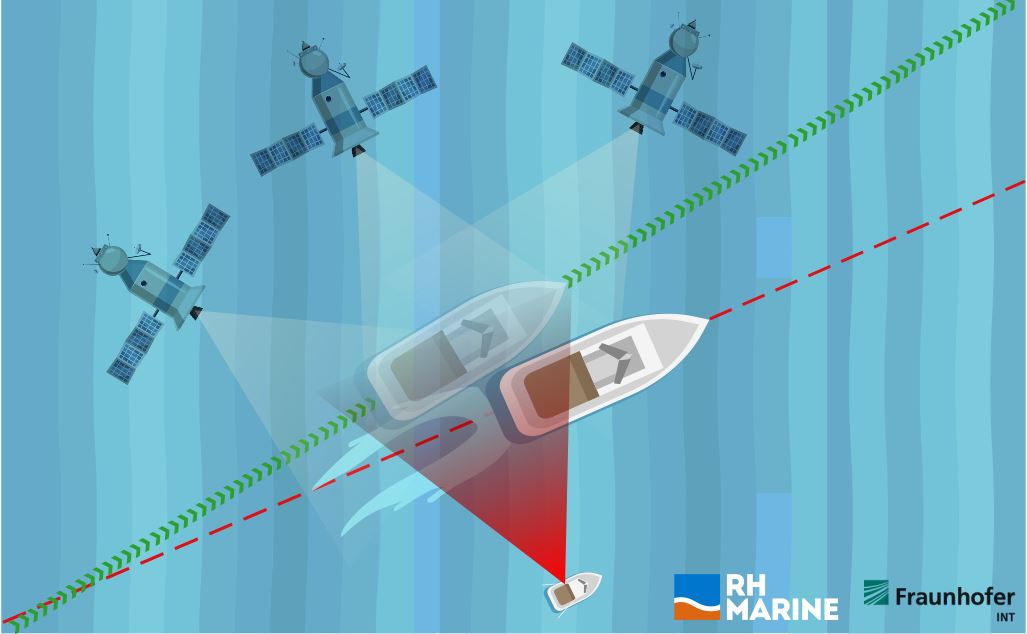
Figure 3: Spoofing as an IEMI threat.
Meaconing is another type of spoofing that requires less technological challenge for the perpetrator. In this form of spoofing, GPS signals are not created with manipulated information but only re-transmitted from a receiver located elsewhere, which could be, for example, another vessel nearby. To this end, the broadcast signals are generally amplified to reach the target GNSS antenna with adequate power levels for acquisition. Although unintentional, there has already been one recorded incident of meaconing that has raised concerns about this threat. In this instance, GPS repeaters used in indoor aircraft hangars unintentionally transmitted their signals to the outside and triggered ground proximity warnings during aircraft take-offs [6].
3) HPEM
High-Power Electromagnetic (HPEM) weapons pose a greater threat to maritime vessels in the sense that there are more attack gateways within a vessel. Unlike jamming and spoofing, where targets are mainly GNSS systems, the HPEM threat can compromise any electronic device in a vessel’s power, communication, and automation systems. From a Critical Infrastructure (CI) perspective, although attacks involving HPEM weapons have a relatively low probability of occurrence, the consequences of such attacks can be highly severe for two main reasons. First, the consequences can vary from interference, DoS, to destruction of electronic devices that perform mission-critical functions [7]. Second, a single attack attempt can affect multiple devices, whose simultaneous failures can trigger adverse system-level effects. Even so, the HPEM threat is still commonly overlooked in CI security plans. One reason for this decision is that there are few publicly disclosed incidents of HPEM attacks, which makes stakeholders believe that this threat is not a priority security issue for their CIs.
HPEM sources can couple electromagnetic disturbances in two modes known as radiated and conducted coupling. In the first mode, the disturbance signal is radiated over the air to reach the internal electronics of a target system. In contrast, in the second mode, the propagation of the disturbance signal is carried out through wires connected to the target system. Regarding bandwidth, the most common types of HPEM sources are narrowband, Ultra-Wideband (UWB), and damped sinusoidal. Apart from the features mentioned above, they can also have different degrees of technological challenge directly related to the assembling technical complexity and component availability. Moreover, depending on the components’ arrangement, they can be big enough to require transportation by truck or small enough to fit in a briefcase [8].
Figure 4 exemplifies a scenario of a radiated HPEM attack on a maritime vessel. The HPEM source is mounted on a small boat and employs an antenna to interfere with the target vessel. In this case, the perpetrators could manually direct the antenna towards the system to be hit. The target could be, for example, the communication antennas located on the deck, the main switchboard protection system on the lower deck, the bridge on the upper deck, among other points of attack. In contrast to the numerous possibilities of radiated HPEM attack gateways, assuming the perpetrator never gets access inside the vessel, conducted attacks are limited to a single scenario. This scenario is represented when the vessel is charging with shore power and a perpetrator injects disturbance signals into the vessel’s cabling, which is connected to the power station. For this case, the risk is generally considered low as most vessels have isolation transformers between their internal circuits and the shore installation, which is a great attenuating medium for electromagnetic interference.
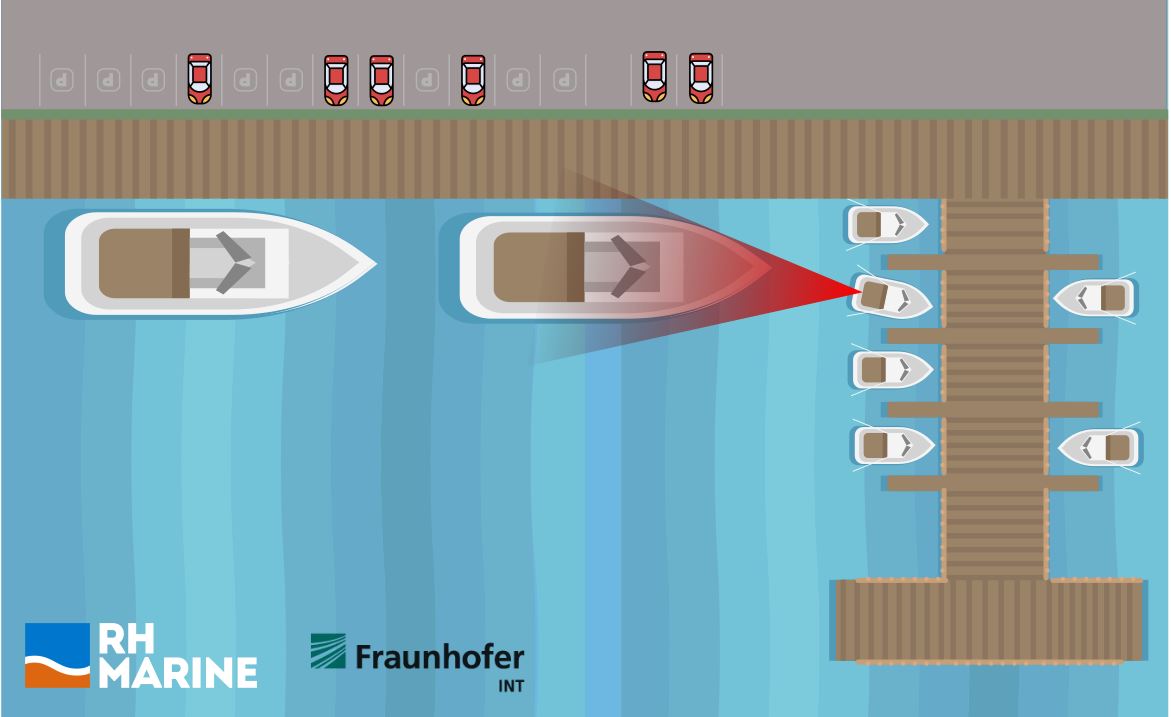
Figure 4: HPEM as an IEMI threat.
Given the threats of jamming, spoofing and HEPM, IEMI attacks should be treated as a relevant security issue in the maritime sector. Successful IEMI attacks on maritime vessels can cause massive economic losses and compromise the safety of individuals on board ships. The risk of such attacks is not only related to the perpetrator’s intent, but also to the different types of IEMI weapons and the particularities of each vessel. In view of this, IEMI risk management processes should be implemented to ensure the safety of maritime vessels. More details on this topic, including guidelines on how to increase the level of IEMI safety of ships, can be found on the paper entitled ”The threat of Intentional Electromagnetic Interference to Maritime Vessels” ([9]) presented at 2022 International Naval Engineering Conference and Exhibition (INEC).

Figure 5: ESR 15 presentation at the 2022 INEC in Delft (Netherlands).
References
[1] ABS Group. ’’FSO Cyber Security Training’’, 2020. Available at: https://www.abs-group.com/News-and-Events/Events/FSO-Cyber-Security-Training/[2] FYFE, Peter; KOVACH, Karl Navstar. GPS Space Segment/Navigation User Interfaces (public release version). Research Corp Fountain Valley CA, 2020.
[3] UBBERS, Barend et al. A Study on the Accuracy of GPS Positioning during Jamming. The International Association of Institutes of Navigation World Congress (IAIN). IEEE, 2015.
[4] GRANT, Alan, et al. GPS Jamming and the Impact on Maritime Navigation. The Journal of Navigation, 2009.
[5] MADRY, Scott. National and International Governmental Policy Issues. Global Navigation Satellite Systems and Their Applications. Springer, 2015.
[6] APPEL, Manuel; HORNBOSTEL, Achim; HÄTTICH, Christian. Impact of Meaconing and Spoofing on Galileo Receiver Performance. The 7th ESA Workshop on Satellite Navigation Technologies NAVITEC, 2014.
[7] SABATH, Frank. Classification of Electromagnetic Effects at System Level. In: Ultra-Wideband, Short Pulse Electromagnetics 9. Springer, New York, NY, 2010. p. 325-333.
[8] LUGRIN, Gaspard et al. Overview of IEMI Conducted and Radiated Sources: Characteristics and Trends. The International Symposium on Electromagnetic Compatibility. IEEE, 2013.
[9] ARDUINI, Fernando et al. ”The threat of Intentional Electromagnetic Interference to Maritime Vessels. International Ship Control Systems Symposium. Conference Proceedings of iSCSS, 2022. DOI: 10.24868/10723
About the Author: Fernando R. Arduini
 Fernando R. Arduini holds a B.Sc. in Electrical Engineering from the Federal University of Triângulo Mineiro in Brazil. He completed part of his studies at the University of Glasgow in the United Kingdom, where he also performed an internship on wind energy integration into the power grid. In 2019 and 2020, respectively, he accomplished his M.Sc. degree in Power Systems and MBA in Business Management with Distinction, both from the University of São Paulo in Brazil. His Master’s thesis was focused on emerging hardware and software Fault Ride-Through strategies applied to DFIG-based wind turbines. In 2019, Fernando worked at CITCEA-Barcelona Tech, Spain, on the modelling and integration of Superconducting Fault Current Limiters applied to smart grids applications.
Fernando R. Arduini holds a B.Sc. in Electrical Engineering from the Federal University of Triângulo Mineiro in Brazil. He completed part of his studies at the University of Glasgow in the United Kingdom, where he also performed an internship on wind energy integration into the power grid. In 2019 and 2020, respectively, he accomplished his M.Sc. degree in Power Systems and MBA in Business Management with Distinction, both from the University of São Paulo in Brazil. His Master’s thesis was focused on emerging hardware and software Fault Ride-Through strategies applied to DFIG-based wind turbines. In 2019, Fernando worked at CITCEA-Barcelona Tech, Spain, on the modelling and integration of Superconducting Fault Current Limiters applied to smart grids applications.


