Communication networks are the backbone of the modern safety-critical systems. Therefore, it is vital to arm these error-prone networks against external disturbances. In this blog, I will discuss the challenges associated with this task in electromagnetic polluted environments.
Often we need to transmit sensitive data such as financial information where every symbol in the message is a vital one. Mistake can corrupt the entire message and no matter how we communicate, we face this complication. Fig. 1 provides an example of such mistakes.

Figure 1 – Example of corruption in banking information
One kind of corruption occurs when a bit flips. The transmitter sends a one but it is received as a zero or a zero which is received as a one. These are called errors or bit-flips. Some instances of bit-flips are demonstrated in Fig. 2.

Figure 2 – Some instances of bit-flips
Another kind of corruption is an erasure which occurs when the bits are so distorted that they are considered unknowns or blanks in the message. An example of such a scenario is provided in Fig. 3.

Figure 3 – Some instances of erasures
At this point, you may ask why and how these corruptions occur. Noise is the main reason for these corruption. Note that any unwanted signal or information is considered as a noise. Noise has two types: natural noise like lightening strike and man-made noise like cellular network. In case of electronic devices, noise could be in the form of electromagnetic (EM) waves. This happens when EM waves are leaked from some electronic device(s), which are also called electromagnetic disturbances (EMDs), and picked up by other devices. Accordingly, EMD with enough energy can lead to corruption.
Within this blog we will solely discuss this problem in terms of bit-flips.
Despite the benefits of new technologies, the rising number of electronic devices have resulted in more EM pollution and more complex EM environments. In an EM-polluted environment, EMD induces additional voltages onto the communication channel which can result in bit-flips in the transmitted data. An instance of this phenomenon is shown in Fig. 4. While some communication channels suffer from less corruption than others it is important to note that corruptions are bound to occur. No channels are truly noiseless. Therefore, the challenge communication engineers will always face is how can we transmit our messages perfectly when we know some symbols will be corrupted in transmission.
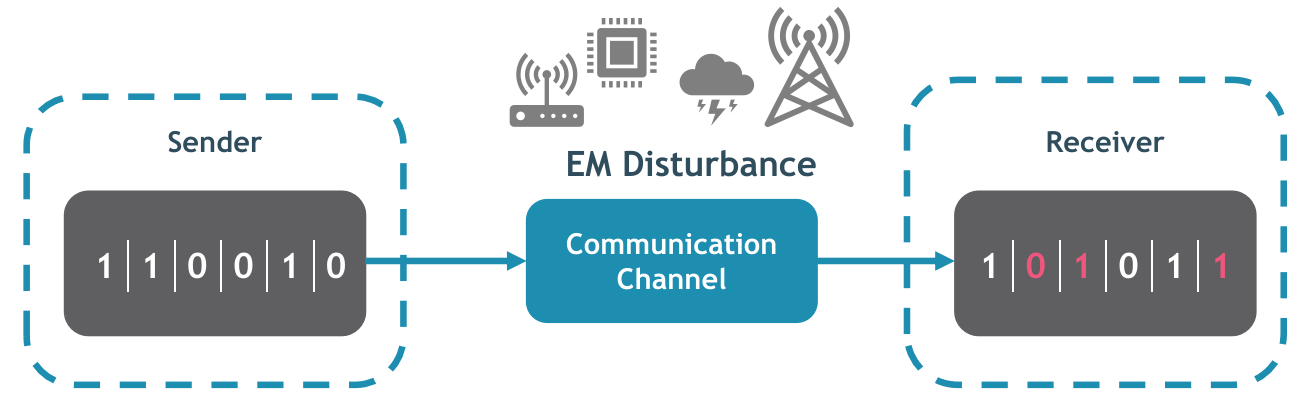
Figure 4 – Negative impact of EMD on the data transmission
Realize we all face this problem during ordinary voice communication when a word is misheard in a conversation. To recover from this corruption we simply repeat ourselves (maybe several times). Technically, this is called a repetition code. It is a simplest error correction code. For instance, if we have a binary message, it would be encoded before transmission into three copies of itself. This might be received with some bit-flips as shown in Fig. 5.

Figure 5 – An example of repetition code
These bit-flips can easily be decoded by comparing the three copies bit by bit and taking the majority vote. Thus the message would be decoded correctly. Besides, this comparison operator is simple and therefore can easily keep up with the speed of communication.
For decades, Error Control Techniques (ECT) have been developed and employed to protect communication networks against a limited number of random bit-flips [1-4]. Forward Error Correction (FEC) is a subgroup of ECT that is commonly used in the physical-layer of the protocol stack. FEC can recover data without asking for re-transmission when a limited number of errors are introduced. Correspondingly, FEC adds extra information to the data at the sender side and generates a codebook (i.e., a dictionary of valid data). This information is later used at the time of decoding to detect and correct the corrupted data. An example of this process is presented in Fig. 6.
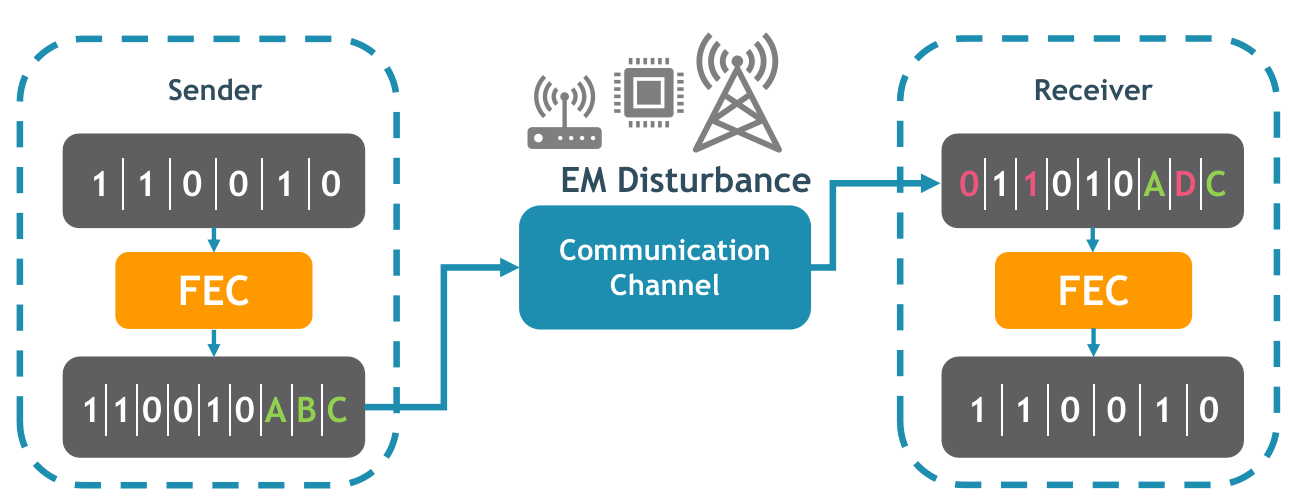
Figure 6 – Positive impact of forward error correction codes during data transmission
FECs, however, have a major vulnerability. In some cases, data can get corrupted in such a way that it turns into another valid data (based on the generated codebook)[5-6]. As a consequence, FECs cannot detect such errors and the decoder assumes that the received data is correct. From the safety perspective, these undetected corrupted data may lead to severe harm to users, bystanders, and the environments.
To conclude, it is crucial to mitigate these undetectable errors to a level as low as reasonably practicable. This task, therefore, is the main focus of my research in which I try to resolve this vulnerability by investigating its origin in various FECs, and developing the EM-resilient version of the considered FECs.
References
[1] R. W. Hamming, “Error detecting and error correcting codes,” The Bell system technical journal, vol. 29, no. 2, pp. 147–160, 1950.[2] I. S. Reed, “A class of multiple-error-correcting codes and the decoding scheme,” Massachusetts Inst of Tech Lexington Lincoln Lab, Tech. Rep., 1953.
[3] R. Gallager,” Low-density parity-check codes,” IRE Transactions on information theory, 8(1), 21-28, 1962.
[4] A. Viterbi, “Convolutional codes and their performance in communication systems”. IEEE Transactions on Communication Technology, 19(5), pp.751-772, 1971.
[5] J. Van Waes, D. Vanoost, J. Vankeirsbilck, J. Lannoo, D. Pissoort, and J. Boydens, “Resilience of error correction codes against harsh electromagnetic disturbances: Fault elimination for triplication-based error correction codes,” IEEE Transactions on Electromagnetic Compatibility, vol. 62, no. 5, pp. 1929–1938, 2020.
[6] P. Memar, J. Vankeirsbilck, D. Vanoost, T. Holvoet, and J. Boydens, “Resilience of Reed-Solomon codes against harsh electromagnetic disturbances: Influence of over-voltage detection,” pp. 868–873, 2021.
About the Author: Pejman Memar
 Pejman obtained his Master’s degree in Biomedical Engineering from K. N. Toosi University of Technology (Iran, 2017) with distinction. For his Master thesis, he proposed a novel algorithm in Sleep Apnea Detection to eliminate the traditional requirements for performing a costly Polysomnogram test on every subject. Furthermore, he has a genuine interest in Data Analytics, Object-Oriented Programming, System Safety, and Embedded Systems.
Pejman obtained his Master’s degree in Biomedical Engineering from K. N. Toosi University of Technology (Iran, 2017) with distinction. For his Master thesis, he proposed a novel algorithm in Sleep Apnea Detection to eliminate the traditional requirements for performing a costly Polysomnogram test on every subject. Furthermore, he has a genuine interest in Data Analytics, Object-Oriented Programming, System Safety, and Embedded Systems.


