In the movie Ocean’s Eleven, starring George Clooney and Julia Roberts, 11 criminals use a physical device called “the pinch” to facilitate a criminal act in Las Vegas. This device is nothing more than a source that emits electromagnetic pulses that can trigger a blackout in a portion of the power grid. From this perspective, the criminals’ goal was to affect the electric grid of the ”city that never sleeps” to facilitate the theft of a safe containing the wealth of three casinos.
This type of criminal act sounds like something out of a Hollywood action movie, doesn’t it? But make no mistake, this threat has a name, it’s REAL and is growing in concern by experts and entities worldwide. This blog will introduce the so-called Intentional Electromagnetic Interference (IEMI) threat and why it should be considered carefully in critical infrastructure security plans.
Figure. 1 – Poster of the Ocean’s Eleven movie. Source: https://www.imdb.com/title/tt0240772/
In order to ensure the proper functioning of electronic-based devices in common electromagnetic environments, the regulatory authorities establish a series of requirements and standards of electromagnetic compatibility (EMC). However, these requirements are often not sufficient to protect critical devices from electromagnetic interference (EMI), a disturbance originating from the outside and affecting the regular operation of electronic and communication devices by coupling into their conducting structures. Depending on scale, minor errors or even full-scale damage could be induced. Sources of EMI are divided into natural and artificial ones. The former is beyond our control and includes lightning and geomagnetic storms. On the other hand, the latter is more frequent and, specifically if neglecting safety distances, could include radio and TV broadcasts, mobile networks, radars, switching converters and power transmission lines, among others. The general EMI mechanism being established, it can be inviting to terrorists, criminal organizations, and adversaries to intentionally interfere with and/or damage systems of critical sectors, such as power systems, telecommunications systems, financial systems, manufacturing, transportation, and water supply [1].
A broadly recognized definition for IEMI was provided by a workshop held at the EMC Zurich Symposium in 1999 [2]:
“Intentional malicious generation of electromagnetic energy introducing noise or signals into electric and electronic systems, thus disrupting, confusing or damaging these systems for terrorist or criminal purposes.”
Figure. 2 – Fictitious representation of a suitcase-shaped IEMI source. Photo: Dan Saelinger; Prop Stylist: Birte Von Kampen [8]
An IEMI source can be classified according to its primary coupling scheme, either radiated or conducted. In the former case, the disturbance signal is radiated over the air to reach the interior electronics of a target system, while in the latter, the propagation of the disturbance signal is carried through conductors connected to the target. Moreover, the following distinction is helpful since it has an impact on possible mitigation measures: The High-power electromagnetic (HPEM) energy can couple to the target either by front-door or back-door coupling [3]:
- Front-door coupling: The electromagnetic disturbances employ available ports and coupling paths designated for the propagation of electromagnetic energy and communication with the external environment. Therefore, these means are not easily shielded against disturbances without losing or severely degrading the system’s functionality. Examples include telecommunication base stations or mobile devices irradiated in their operative wireless bands.
- Back-door coupling: The electromagnetic disturbances use coupling paths not destined for communication with external surroundings. These coupling paths are represented by external wiring, openings for drainage and ventilation, as well as imperfections in the shielding structure.
So, why do experts think that the IEMI threat to today’s society has increased over the years? Here are a few aspects which indicate an answer to this question.
- Over the last few years, we have seen an increasing miniaturization of electronic circuits. From 1971 to 2008, this miniaturization jumped by almost a factor of 1000, when for example an Intel 4004 chip that used 10 µm processing technology on first release reached 45 nm resolution. As electronic products have become physically smaller while offering greater functionality at lower costs, increased clock frequencies and decreased voltage levels have possibly led to greater vulnerability to electromagnetic interference. Aligned with this, many critical infrastructures are nowadays supervised and controlled by sensitive electronic equipment part of Supervisory control and data acquisition (SCADA) systems. These systems encompass computers, communications devices, Programmable Logic controllers (PLC), among other devices, which can be vulnerable targets to IEMI [4].
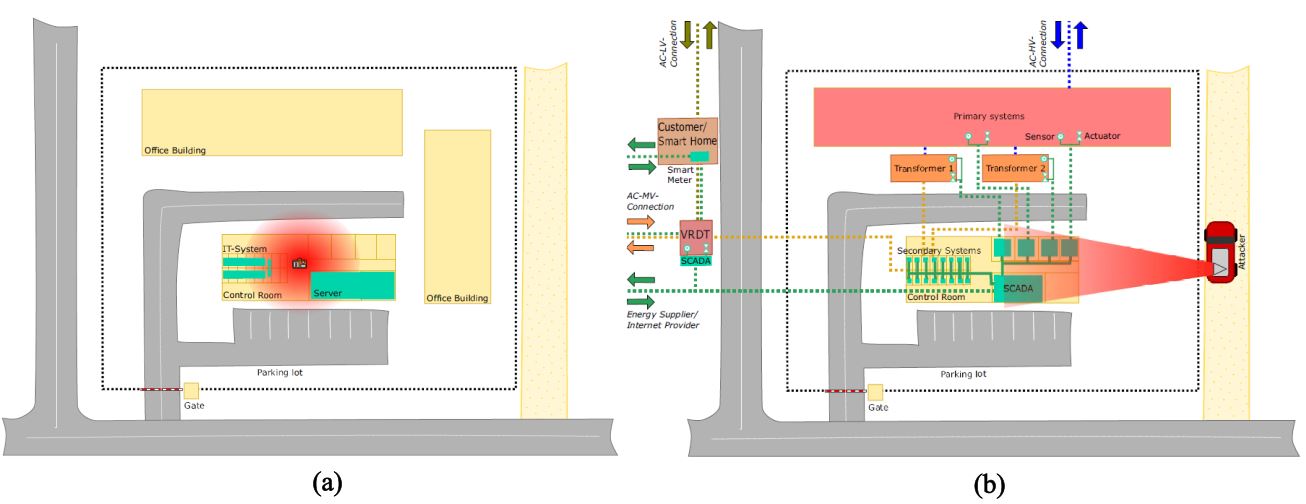
- The quantity of identified IEMI sources is already very vast and comprehensive. In 2014, [5] identified 76 different types, in which 21 were conducted sources and 55 were radiated ones. These sources have different characteristics, including band type, average/center frequency, peak voltage (for conducted sources) or peak field (for radiated sources), among other features. Besides distinct technical characteristics, they may present different non-technical features that make the IEMI risk management process even more challenging. These non-technical characteristics are represented by the technology level needed to assemble the source, the cost level and the mobility in approaching the target system. As illustrated in Figure 3(a), a source can be suitcase-shaped, where in a fictitious scenario, it is placed close to critical equipment in a substation control room. Similarly, as shown in Figure 3(b), the source can be mounted on a car, which is parked outside the critical infrastructure premises, and emits interference signals towards the target system employing a larger scale antenna.
Figure. 3 – IEMI sources of different levels of technology and portability. Source: [6].
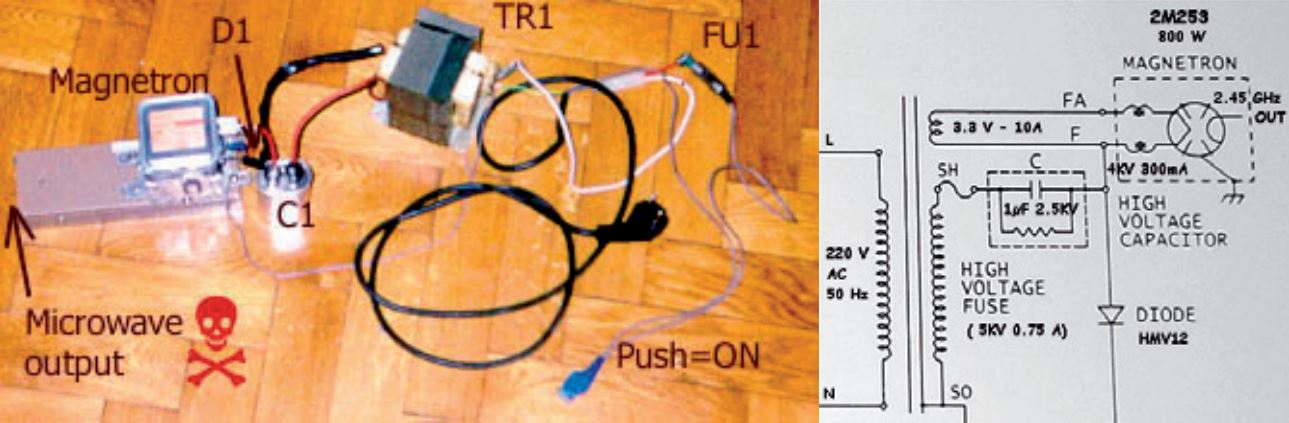
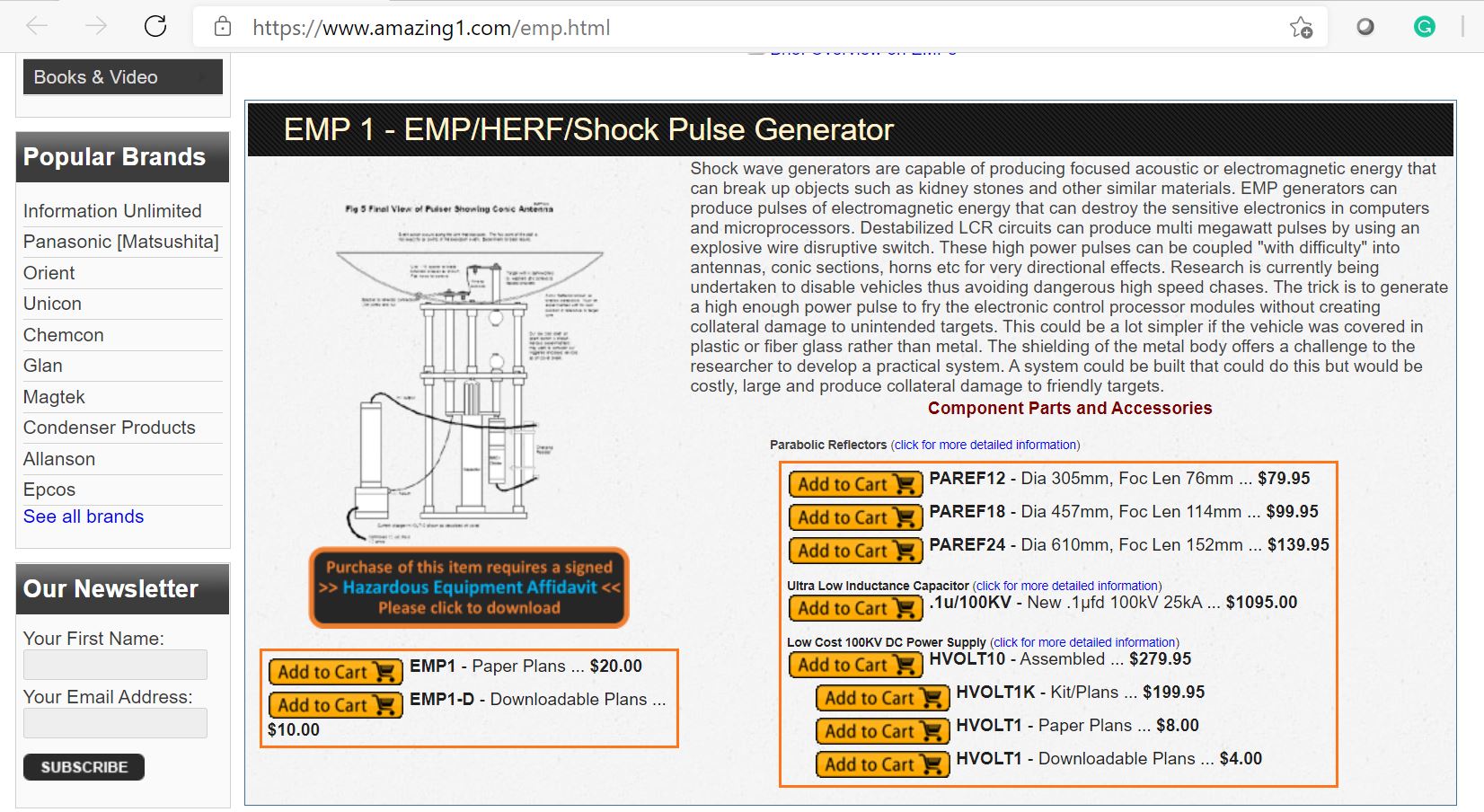
- Many EMI-generating sources can be easily built or purchased by hobbyists. The internet itself provides many tutorials on how to build sources using off-the-shelf components, such as microwave magnetrons, capacitors, and switches. Therefore, any individual with some base technical knowledge is able to obtain their own homemade source. Alternatively, already assembled sources can be purchased from various websites, further reducing the offenders’ effort [7]. Figure 5 shows a picture and circuit diagram of a homemade source found on the internet. Figure 6, on the other hand, illustrates an EMP pulse generator advertised for sale.
Figure. 4 – Picture and circuit diagram of a crude homemade electromagnetic source found on the internet. Source [7].
Figure. 5 – EMP pulse generator advertised for sale. Source: https://www.amazing1.com/emp.html
- IEMI attacks are silent and do not attract attention. Compared to a physical terrorist act (e.g., involving the use of explosives), an electromagnetic attack can easily occur unnoticed and at a distance from critical equipment and/or systems. Similarly, unlike a cyber-attack, in which a hacker could set off alarms while trying to bypass firewalls, an IEMI exposure typically leaves no footprint on the affected system. To make matters worse, the system operator only becomes aware of an IEMI attack when the consequences appear, making it difficult to take any countermeasures. And even then, the observed detrimental effects might incorrectly be blamed on generic hardware or software failures, preventing even basic awareness of an attack being perpetrated. From this perspective, this threat can pose major risks to public safety, especially concerning critical sectors that drive society [8].
Figure. 6 – Fictitious photo of an IEMI attack. Photo: Dan Saelinger; CGI: Swell; Prop Stylist: Birte Von Kampen [8]
Despite the growing concern about IEMI by experts in the field of EMI, this threat is still generally overlooked in critical infrastructure security plans [9]. One of the reasons is that there are few publicly disclosed incidents, which may give the impression to critical infrastructure operators that IEMI is not so relevant. Apart from the fact that it is difficult to identify an electromagnetic attack by itself, many incidents employing electromagnetic weapons might not be reported in order not to expose the vulnerability of the affected system, as well as not to damage the image of the affected organizations.
From the few incidents circulating in the media and scientific literature [7] [10], one can cite the following in order to get a basic impression of occurrences:
1) North Korea has been accused of producing jamming signals near its border with South Korea in order to affect the GPS navigation systems of several means of transport of the neighboring country. As a result, although fortunately no fatalities have been attributed to the incident, more than 300 commercial flights to and from two South Korean airports, as well as more than 100 ships, had their navigation units affected.
2) In Moscow, a telecommunications system has been disrupted due to a remote injection of voltage into a telephone line. As a result, the telephone connection of more than two hundred thousand customers was interrupted for 24 hours.
3) In Japan, criminals have employed an EM disrupter to interfere with a gambling machine (Pachinko) in order to trigger a win falsely.
4) In St. Petersburg, an EM disruptor has been used to facilitate the robbery of a jewelry store, where the offender’s motivation was to disable the facility’s security system.
5) In the Netherlands, a disgruntled customer disrupted a local bank’s IT network after being refused to be granted a loan.
6) In Kizlyar, Dagestan, Russia, Chechen rebels have affected police radio communication using RF jammers during a raid.
7) In several European cities (e.g., Berlin, Vienna), criminals have employed GSM-Jammers to disable the security system of limousines.
8) In Russia, Chechen rebels have used an EM disruptor to disable a security system and access a controlled area.
9) In London, the UK, employees of a local bank have been blackmailed by an individual who threatened to use EM disruptors against the bank’s IT system.
Given the above examples, it is understandable that research is conducted in this area on a continuous basis in order to probe for vulnerabilities and to develop mitigation measures. Some protection can be achieved in limiting the accessibility of crucial electronics, and applying filtering and shielding where appropriate. Since it might not be possible or economical to prevent any and all disturbances from coming through, the concept of EM resilience has recently come more into focus, where the ability to degrade gracefully to some minimum stable state might help out in ensuring facility operations, possibly complemented with a healthy redundancy concept.
References
[1] Ivezic, M., ‘’The Growing Threat of Intentional Electromagnetic Interference (IEMI) Attacks’’, 2018. Available at: https://www.linkedin.com/pulse/growing-threat-intentional-electromagnetic-iemi-attacks-marin-ivezic.
[2] Giri, D. V., Frank Sabath, and Richard Hoad. High-Power Electromagnetic Effects on Electronic Systems. Artech House, 2020.
[3] Bäckström, Mats G. “The threat from intentional EMI against the civil technical infrastructure.” Reprint from ESW2006, 3rd European Survivability Workshop. 2006.
[4] Månsson, D. Susceptibility investigations and classification of civilian systems and equipment. Doctoral dissertation. Université d’Uppsala, 2008.
[5] Mora, N., Vega, F., Lugrin, G., Rachidi, F., & Rubinstein, M., Study and classification of potential IEMI sources. System Design and Assessment Notes, 41, 2014.
[6] Lanzrath, M. HPEM-Verwundbarkeit des Smart Grid. Doctoral dissertation. Universität Duisburg-Essen, 2020.
[7] Sabath, F. “What can be learned from documented Intentional Electromagnetic Interference (IEMI) attacks?.” 2011 XXXth URSI General Assembly and Scientific Symposium. IEEE, 2011.
[8] Radasky, W. ‘Electromagnetic Warfare Is Here’’, 2018. Available at: https://spectrum.ieee.org/aerospace/military/electromagnetic-warfare-is-here.
[9] Ivezic, M., ‘’Intentional Electromagnetic Interference (IEMI) – the overlooked threat to IoT’’, 2018. Available at: https://www.csoonline.com/article/3269509/intentional-electromagnetic-interference-iemi-the-overlooked-threat-to-iot.html.
[10] GPS World, ‘’The Growing Threat of Intentional Electromagnetic Interference (IEMI) Attacks’’, 2012. Available at: https://www.gpsworld.com/massive-gps-jamming-attack-by-north-korea/.
Author: Fernando Rebeiro Arduini