As Electromagnetic Interference threats are evolving rapidly, one big question remains unanswered: what is the behavior of Error Detection and Correction Codes under harsh electromagnetic interference?
This blog provides a solution to facilitate this exploration.
What is Electromagnetic Interference?
Each electronic device emits an electromagnetic (EM) field, that could cover a large area. When two or more electronic devices are placed in each other vicinity, each device exposes the other devices to its radiated radio frequencies (RF). When these emitted radio waves are powerful enough, they can disrupt the normal operation of the afflicted device, as shown in Figure 1. This phenomenon is called Electromagnetic Interference (EMI). To give you an idea, EMI effect can affect speakers to make a high-pitched noise when they are placed near a ringing phone.
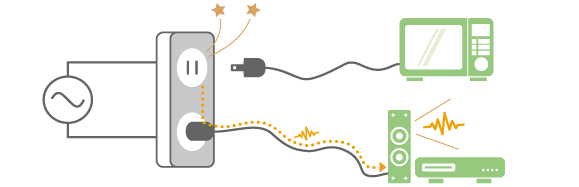
Figure 1: Example of electromagnetic interference (source: www.murata.com)
What are the Electromagnetic Interference sources?
There are two types of electromagnetic interference sources: natural and man-made sources. Figure 2 demonstrates some examples of EMI sources. Either of EMI sources are able to generate rapid alternating current and voltage that can cause interference. Solar storms and lightening are the most significant natural sources. EMI sources associated with man-made technologies are numerous; cellular network, satellite, power lines, and ignition systems are a few examples of this category.
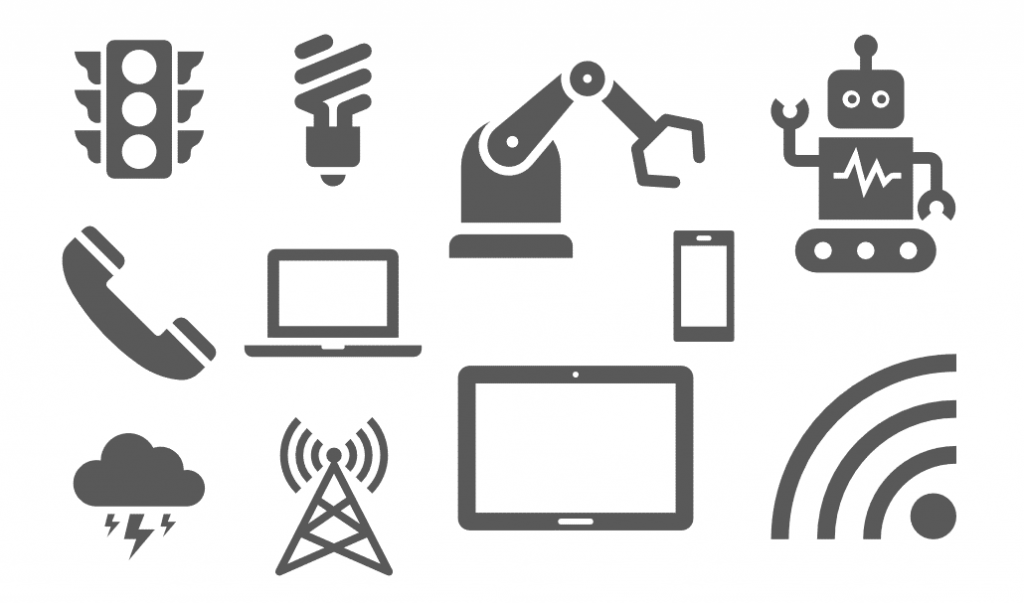
Figure 2: Some examples of EMI sources
What are the effects of Electromagnetic Interference?
Electromagnetic Interference can affect systems to under-perform or even to prevent them from working. In turn, this might lead to the violation of safety goals, and can therefore induce grievous harm to users or the environment. It is thus vital to be aware of EMI and take adequate measures to prevent the failure of safety-critical systems. From the communication channel perspective, EMI is able to induce alternating voltage on traces and generates bit-flips in the communication as shown in Figure 3.
Bit-flip: The switching state of one bit from 0 to 1 or vice versa is defined as bit-flip or bit manipulation. For instance, if 1101 turns to 1111 then we can say that 1 bit-flip occurred at index 1.
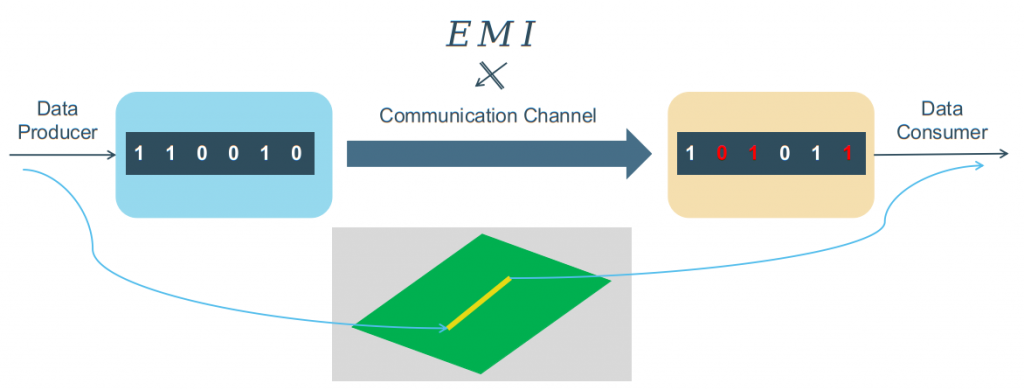
Figure 3: EMI effect during transmission
What are Error Detection and Correction Codes?
Error Detection and Correction Codes (EDCCs) are hardware-based setup or software-based signal processing approaches to detect and correct errors. Nowadays, EDCCs are used in various domains of technology from communications such as internet and mobile phones to advertisement using QR codes. These techniques work in two steps. First, they detect the errors caused by interference during transmission from producer side to the consumer side. Then, they try to fix the errors and reconstruct the error-free data.
Why are Error Detection and Correction Codes required?
As mentioned earlier, EMI is capable of generating bit-flips during communication. Therefore, at least one layer of software (such as EDCCs) or/and hardware protection is required throughout the communication. Accordingly, EDCCs take advantage of redundancy (i.e., adding extra information as parity to the original data, which is called encoding) to detect error and recover lost information as illustrated in Figure 4.
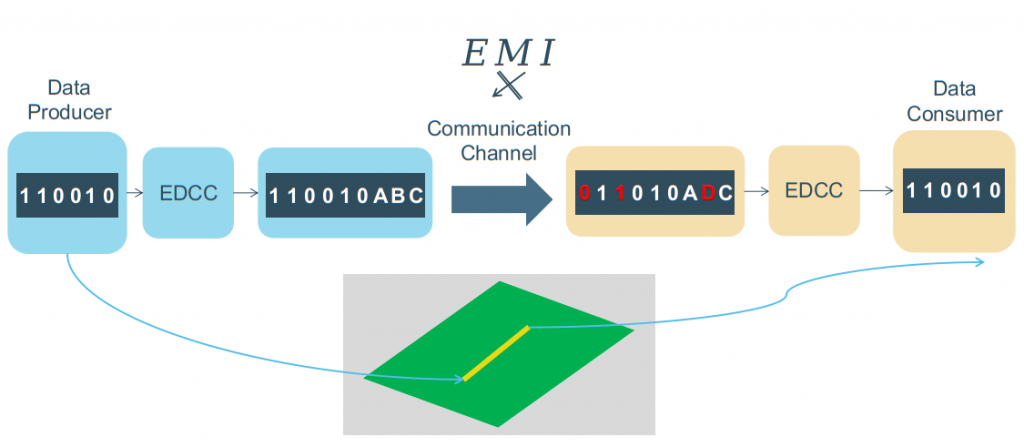
Figure 4: An Error Detection and Correction Code in data communication
How to simulate the Electromagnetic Interference effect on the Error Detection and Correction Codes and why we need such a simulation?
Allow me to answer the why question first and then address the how. As previously stated, EMI is able to affect data communication and yield errors during transmission. Furthermore, we indicated that EDCCs have a capability of detecting and correcting errors, but thus far, no deterministic way has been proposed to investigate the behavior as well as vulnerabilities of EDCCs under harsh EMI. In this regard, the remaining parts of this blog are addressing the how question.
One straightforward approach to demonstrate the EMI effect on the transmitted data is to apply a single sine wave as an interference to a data word during transmission. The setup of this simulation will be covered in the next section.
Software-based setup for generating Electromagnetic Interference effect
Assume the following bit stream, which is to be transmitted at a rate of 5 bits per second (BR = 5 bps):
Input Bit string: [1,0,1,0,1]
The following steps represent a way to simulate the EMI effect on this bit string:
- Generate a sine wave with desired parameters:
Here: Amplitude = 1V, disturbance frequency = 5 Hz and phase = 90°- sine wave = Amplitude × sin( [ 2π × time × disturbance frequency] + phase )
- time is in the range of 0 and ( [1 / BR] × length of bit string); here: between 0 and 1 s.
- Add sine wave to the Input Bit string;
- Sample the data exactly at the middle of each bit;
- Specify a threshold to turn the voltage into 0 or 1.
Here: any voltage higher than or equal to 0.5 V is turned into 1, and voltages lower than 0.5 V are turned into 0.
The output of step 4 might be untouched or it could contain bit-flips like this specific setup, which represent the EMI Effect. The above mentioned steps are illustrated for a specific setup in Figure 5.
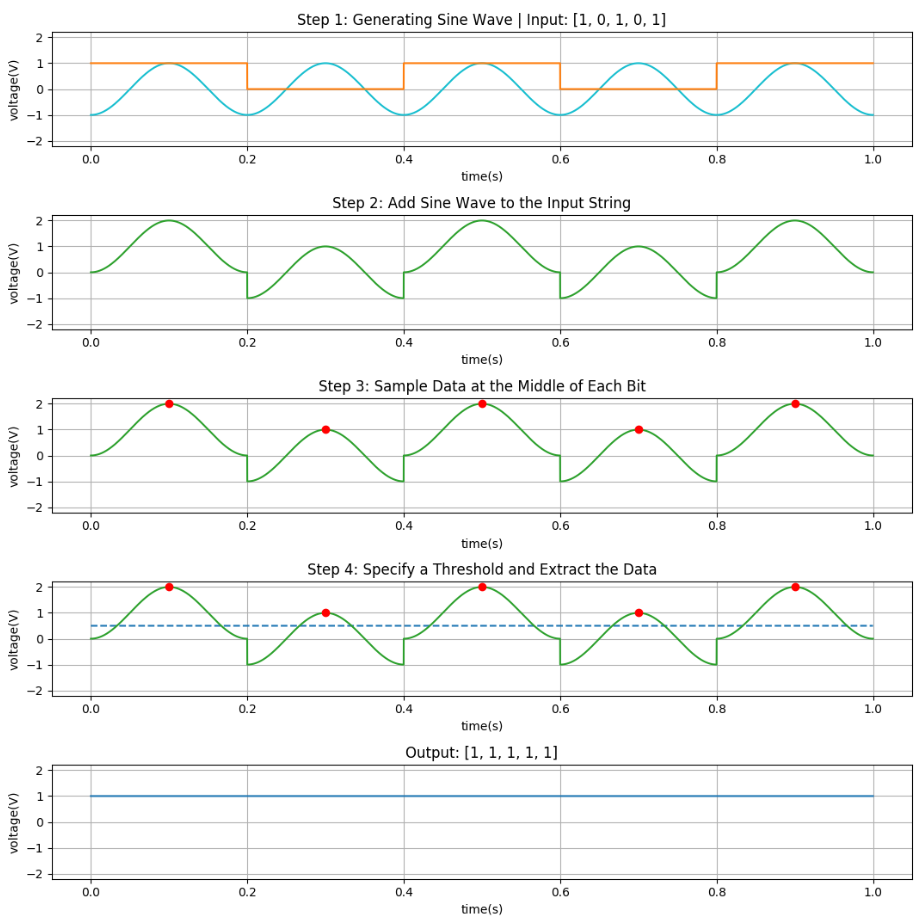
Figure 5: Steps for simulating EMI effect
In order to investigate the behavior of EDCCs under EMI effect, we just need to implement this approach while these techniques are under operation (i.e., after transmitting encoded data and before decoding) and check their output under different circumstances to figure out their behavior and to uncover possible vulnerabilities.
Conclusion
The main goal of this blog was showing the importance of electromagnetic interference and its negative effects on the data communication, as well as providing an approach to simulate this effect on EDCCs. Although, EDCCs are designed for detecting and correcting errors, yet there is not a deterministic way to explore the behavior and vulnerabilities of these techniques under harsh EMI. These simulations will provide beneficial insights regarding the behavior of EDCCs, specifically when they have been using in safety critical systems.
About the Author: Pejman Memar
 Pejman obtained his Master’s degree in Biomedical Engineering from K. N. Toosi University of Technology (Iran, 2017) with distinction. For his Master thesis, he proposed a novel algorithm in Sleep Apnea Detection to eliminate the traditional requirements for performing a costly Polysomnogram test on every subject. Furthermore, he has a genuine interest in Data Analytics, Object-Oriented Programming, System Safety, and Embedded Systems.
Pejman obtained his Master’s degree in Biomedical Engineering from K. N. Toosi University of Technology (Iran, 2017) with distinction. For his Master thesis, he proposed a novel algorithm in Sleep Apnea Detection to eliminate the traditional requirements for performing a costly Polysomnogram test on every subject. Furthermore, he has a genuine interest in Data Analytics, Object-Oriented Programming, System Safety, and Embedded Systems.


